Franklin D. Roosevelt famously said the only thing we have to fear is fear itself. This appears to be true when it comes to wireless security. Whether real or groundless, security fears and concerns delay and often scuttle otherwise justifiable wireless projects.
Much fear, uncertainty, and doubt (FUD) exist when it comes to wireless security. The best way to overcome this is to acknowledge its existence, find out how and where it originates, and see how it affects new wireless projects. These insecurity levels then can be reduced by looking at best practices in wireless security.
The best FUD gauge is the collective opinion of end users and the consultants who serve them as these groups control the purse strings and the rate at which industrial wireless projects proceed. “Wireless networks are more accessible than wired networks,” says Gary Crenshaw, senior electrical engineer with Beam Global Wine and Spirits, part of Fortune Brands in Lincolnshire, Ill. “A wireless network in a populated area is more likely to be hacked than a network in a remote area, simply because there are more people and more computers in populated areas, and it is harder to limit signal strength and access.”
Mark Atanasoff, principal electrical engineer at Osram Sylvania, is another end user who is also concerned with unauthorized access. “Inherently, wireless networks are not and cannot be as secure as their wired counterparts,” says Atanasoff. “You can control bits flying through a wire, but it is harder to keep a handle on bits flowing through air. But without intimate knowledge of how the wireless system is set up—such as frequencies, addressing, and protocols—it would be difficult to steal any usable data.”
The risks can be minimized. “Wireless never can be as secure as wired networks, but there are techniques to make them secure enough for automation projects,” argues Dick Caro, certified automation professional and CEO of CMC Associates, Hanover, Mass. Caro is a consultant in the field and works with ISA to develop wireless standards that will include built-in security.
Atanasoff makes a good point by separating access from understanding what accessed data means. There are two main components to security on any network. The first is controlling access, and the second is encrypting information. An analogy can be drawn to eavesdropping on a conversation. Proximity to the speakers gives access, and understanding the language breaks the encryption.
It might be easier to access a wireless network than it is to access a wired network, but this relatively easy access has been turned from a wireless weakness to a wireless strength. Because physical access to wired networks can be controlled, at least in theory, most wired networks don’t use message encryption.
On the other hand, wireless networks look at unauthorized access as an ongoing threat, and most wireless applications employ sophisticated encryption to prevent damage from access. “What would someone do with an intercepted and encrypted data packet?” asks Chris Gibbons, engineering associate with Sasol North America, a specialty chemicals producer in Houston.
Most end users don’t think wireless is quite as secure as all that. But overall, many think that wireless security is good enough right now for industrial applications.
Vendors Optimistic
Wireless vendors are even more optimistic. They know that overcoming security concerns is key to selling wireless products, so they have devoted lots of time and money to wireless security. “The majority of wireless networks available today are protected by the Advanced Encryption Standard (AES), which provides a high degree of security against external threats,” says John Guite, division engineering manager at Parker Hannifin. “Additionally, non-Ethernet-based wireless networks such as ZigBee are protected further because they are personal area networks. A PAN requires a potential hacker to be in relatively close proximity—usually within the facility—to detect the network, further protecting the integrity of the network.”
Part of making a network secure is keeping it up and running. “Wired communications are subject to damage from digging, collisions with mobile machinery, animals eating cable insulation, or degradation due to weather,” observes Ira Sharp, product marketing specialist with Phoenix Contact. “The absence of readily damaged cables is a big advantage with wireless communications.”
A main cause of wireless FUD is poor implementations of wireless security measures in the past. “Obviously, one can set up a completely unsecured wireless network by turning off the security features,” says Joel Young, vice president of R&D and CTO of Digi International.
As Young hints, end users bear considerable responsibility for securing wireless networks. Wireless products often are delivered by vendors with security features disabled to ease initial setup and let end users customize security for their particular needs. Unfortunately, some end users don’t follow proper procedures to activate the security features.
“End users must perform an initial security assessment to determine what level of security is needed,” adds Young. “They must then use available security tools, just as with wired networks. In practice, many wireless network installations actually are more secure than their wired counterparts because end users have become paranoid enough about wireless that they actually perform the security assessment. On the wired side, many are lulled into a false sense of security. Keep in mind that most security breaches are not from some sophisticated form of electronic listening, but rather due to a failure to use basic authentication systems effectively.”
Security Concerns Limit Implementation
Some end users have significant concerns about wireless security, while others are more sanguine. But both camps see security as a limiting factor for wireless projects.
“Concerns about wireless security are absolutely holding up projects,” thinks Eric Byres, PE, principal at Byres Security . “People are scared of technology issues they do not understand clearly, and wireless security is one of those issues.”
End users agree. “Wireless networks are considered less safe than wired networks,” believes Earl Sullivan, executive vice president of operations at pharma firm RxElite. “People often are more comfortable with what they know, and what most people know are wired networks.”
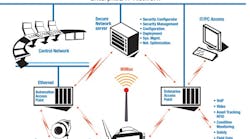
Secure Entry: This diagram shows how a firewall can be used to secure communications between a wired Ethernet network and a plant wireless network.
Even when the automation group understands and is comfortable with wireless, other company departments can step in and put a damper on projects. “At our company, wireless networks currently are unconditionally banned by the network administrators as an unnecessary risk,” relates Jeff Waufle, IT technical services supervisor at Southern Nevada Water Systems.
An end user at a major pharma company requesting anonymity has no doubt that security concerns are scuttling wireless projects at his company. “Pharma companies institute very tight controls for personnel access to rooms, process centers, and general files,” the user says. “Wireless is such a broad area that trying to keep up with how the many suppliers limit access slows down the product review process. We are required to evaluate the wireless technology specified and to review the project impact. In many cases, just having to perform the evaluation process for a particular wireless specification will kill the project.”
Vendors might have a vested interest in minimizing security worries, but they certainly realize the legitimacy of end user concerns. “Folks are approaching wireless cautiously for good reasons,” says Hesh Kagan, director of strategic marketing at Invensys Process Systems and the president of the Wireless Industrial Networking Alliance. “While wireless networks are capable of being highly secure and robust, they require proper and thoughtful engineering that might not be available to the end user. End users are left to see for themselves the level of security available and the value of the associated applications. There is a lot of FUD in the marketplace regarding wireless, so it’s only natural that end users are cautious.”
Fight the FUD
Wireless security concerns are real, and these concerns are slowing wireless implementations. The best way to address these concerns is to apply industry best practices to wireless security.
Factors Holding Up Wireless Projects
1 Security concerns
|
One would expect vendors to profess expertise in wireless security best practices, but end users also had plenty to say on the subject. “Wireless networks can be made secure by closing unneeded ports and services, by encryption, by limiting access to specific MAC addresses, by using secure socket layer, and by using firewalls at the remote devices as well as at the base station,” says James Batug, engineer with PPL Generation, a PPL subsidiary that operates power plants in the northern United States. “These security measures work, but they must be added to project costs and weighed against wireless benefits.”
Batug’s point about the cost of wireless security measures is a good one, as is the understanding about how security can degrade performance. “We secure our wireless networks by employing authentication methods,” says Harry Silverman, assistant vice president of corporate engineering at L’Oreal USA, New York. “Although our approach to security does work, it slows things down on the network.”
Caro has more to say about wireless security. “A big part of security is the guarantee that every message reaches its intended destination,” he states. “Some users are worried about the use of high-power broadband jamming that could interrupt wireless communications. Such sabotage or terrorism methods technically are feasible and can be done with inexpensive radio equipment that broadcasts white noise at key radio frequencies used by industrial wireless networks. Part of the design for an industrial network standard such as ISA100 is to include spread-spectrum protocols that have been demonstrated to work well in the presence of white noise.”
Security Risks With Wireless Networks
1 Hackers can jump on a network without a
|
End users also are on board with spread spectrum. “Wireless security can be assured by using the latest technology such as frequency-hopping, spread spectrum (FHSS),” says Terry McDonald, automation manager at pharma giant Abbott, North Chicago, Ill. “But the IT wireless folks must be convinced, and I also think there still might be concerns regarding interference from other wireless devices such as walkie-talkies.”
According to Crenshaw at Beam Global Wine and Spirits, wireless security best practices also must encompass IT. “No network is totally secure; but limiting signal strength to not extend beyond your controlled plant area, limiting access only to the required nodes, and using a firewall and router with the latest security features all help,” he says. “One of the most important things is to get help with the security from the IT department, because they look for things that a control engineer might miss.”
Secure Architecture: Network security can be controlled with secure servers and access points. This type of system gives access only to authorized devices.
The right security helps, as does the fact that most hackers just aren’t that interested in industrial networks. Harry Forbes, senior analyst with the ARC Advisory Group, says most Internet-era criminals have the same thinking as Willie Sutton did in the 1920s. Sutton was asked why he robbed banks, and is alleged to have replied, “Because that’s where the money is at.” Even though hackers use higher technology than 1930s bank robbers, Forbes says they have the same motivations. Many end users agree with Forbes and conclude their networks aren’t prime targets for most hackers.
“For a remote tank farm SCADA application, hackers have very little interest to interrupt or steal data, so our concern is RF noise affecting system reliability and integrity,” says Rick Hakimioun, senior instrument/electrical control systems engineer with Paramount Petroleum.
Best Practices for Wireless
1 Limit coverage area
|
Wireless vendors say appropriate security technologies are available, but there is more to security than technology. “Security must be looked at as a broad discipline encompassing a number of functions and technologies,” says Ian McPherson, vice president of products at Moffett Field, Calif.-based wireless network designer Apprion. “The fundamental technologies for network security are link encryption, data encryption, key management, intrusion detection, rogue device detection, service set identifier suppression, authentication, virtual private networks, and network partitioning and segmentation. These technologies and systems are essential and well-understood by security professionals, but need to be coupled with strongly enforced management of the wireless infrastructure and a codified process for monitoring and managing security.”
Security can be applied at several different layers of communications with standard technology, adds Roland Acra, president and CEO of Arch Rock, a San Francisco company that integrates wireless sensor network data into enterprise data. “At the link layer, the lowest layer of transmission, security can be applied with AES-128, a part of the IEEE 802.15.4 wireless specification,” says Acra. “At the network layer, for end-to-end security between the pair of communicating nodes or across several wireless or wired networks, IP security can be used. Finally, at the application layer, security can be enforced with techniques such as SSL and Secure HTTP that are used to selectively secure individual Web-based communications.”
Jeff Becker, global director of wireless business development for Honeywell Process Solutions offers some best practices for encryption and authentication, saying, “We believe the best design provides device-unique and dynamically generated keys at the plant site. These keys must be implemented such that the key contents are easy to deploy, time-limited, and not exposed in plain text to installing technicians. This procedure maintains an always-secure posture and severely limits the probability of a key compromise.”
One of the attractions of wireless in the commercial world is easy access, but access must be limited for industrial applications. “Free Wi-Fi is great at the local Internet cafe but on the factory floor confidentiality and integrity are paramount,” observes Cliff Whitehead, manager of strategic applications at Rockwell Automation.
“Automation professionals should leverage IT department expertise to make sure proper security measures are in place. It does no good to secure the wireless media when other paths of intrusion such as intranets and the Internet are not protected as well,” continues Whitehead.
It’s Not Just Security
While security concerns definitely are holding up wireless projects, other concerns are more pressing for many. “Wireless security is one factor holding up some wireless projects, but reliability is another concern,” says John Blanchard, nonwovens process control leader at DuPont, Wilmington, Del.
Mark Atanasoff, principal electrical engineer at Osram Sylvania, says his company isn’t as concerned about security as it is about the reliability of the technology itself. “We ‘ve not been successful the couple of times we’ve tried wireless, as it was unreliable,” he relates.
While newer wireless implementations might improve reliability, wireless in general is not as reliable as wireline. Just compare frequent lost calls on cell phones to extremely rare lost calls on wired home phones to get a good indicator of the reliability issues that still plague wireless.
Nonetheless, there are some applications where wireless actually is more reliable than wired. “There are wireless Profinet applications where slip rings are not adequate to conduct a signal, especially after some wear has occurred,” observes Carl Henning, deputy director of Profibus and ProfiNet in North America. “Gantry crane motion, for example, can wear out festooned cables, and often it is not practical to fit automatic guided vehicles with tethers.”
Two other issues holding up wireless projects are integration and battery life. “There are a wide range of wireless sensors and networks available from some innovative startup companies and established sensor companies, but these technologies are challenging to integrate into wired systems,” says Robert Jackson, PAC and HMI product marketing manager at National Instruments.
Limited battery life limits performance and longevity of remote devices, adds Jackson. “Wireless adoption will be more widespread when lower-powered intelligent devices can wake up and perform acquisition and data processing, transfer data to the host, and return to sleep to conserve battery life,” he argues.
Security, reliability, and other issues hinder wireless, but perhaps the most significant problem is a lack of standards. The right standards can go a long way toward addressing security concerns and also will offer improvements in many other areas.
“I think wireless security concerns are a minor factor,” says networking expert Dick Caro of CMC Associates in Hanover, Mass. “In fact, most wireless projects actually are waiting for an industrial wireless standard, which the users expect will have built-in security.”
Vendors agree that standards are critical. “The biggest reason why wireless projects are being held up is a lack of standards,” says Paul Sereiko, CEO of AirSprite Technologies, a wireless infrastructure firm in Marlborough, Mass . “End users expect wireless standards will include security along with test suites to verify conformance.”