Network access and security always has been about keeping out what you don't want to get in, but these days it's also about finding and eliminating what got in but shouldn't be there.
Jim Montague is the executive editor for Control. Email him at [email protected].
So, while passwords, encrypted data, segmented networks, and managed Ethernet switches as firewalls are all essential, they're just the start of what it takes to make industrial networks and control applications secure. In the past few years, some viruses, worms and other malicious software have been modified to circumvent the usual barriers, exploit patching schedules, while others like Stuxnet and similar copycats can conduct man-in-the-middle attacks in which they pose as authorized entities, while rewriting critical software behind the scenes.
SEE ALSO: How Much Network Access Should You Allow
"There's no such thing as security-by-obscurity or truly air-gapped systems," says Eric Cosman, engineering consultant at Dow Chemical and co-chair of the ISA-99 industrial cybersecurity committee. "Even in cases where a control system doesn't have a network connection, it's possible to compromise the system by simply inserting an infected USB drive. There's no substitute for understanding your systems, how they're configured, and what your vulnerabilities are."
Consequently, all data and communications from the plant floor to the business level must be monitored and inspected for unauthorized and unusual activity. Luckily, increasingly capable and inexpensive microprocessors, software and hardware components make these network protection and detection devices usable by everyone. These security tools include IT-based network sniffing tools, deep packet inspection software, and a variety of other devices and methods that evaluate whether data and communications on a network is really supposed to be there or not.
Secure Container Shifting
For instance, Europe Container Terminal runs 265 driverless container vehicles, 127 storage cranes and 36 container gantries 24/7/365 to move 7 million tons of goods per year through the Port of Rotterdam. However, all this automated loading and unloading of 20-foot, equivalent-unit containers requires a huge amount of logistical coordination and reliable hardwired, wireless and fiberoptic networking, especially between the cranes and AGVs and their network servers and redundant computing centers.
"The independent crane controls require protection from any type of network interference from human error to denial-of-service attacks," says Ingo Hilgenkamp, product marketing manager for I/O and networks at Phoenix Contact Electronics. "However, this security mechanism must not prevent ECT's operators from switching to backup radios if a malfunction occurs in the fiberoptic cables, which wind onto and off of large reels."
To safeguard communications and make sure the cranes and AGVs precisely execute only authorized commands from operators, ECT implemented Phoenix Contact's mGuard Ethernet switches/firewalls, security appliances and mechanical components, which are prewired, configured and DIN-rail mounted (Figure 1). Based on a hardened embedded Linux operating system, mGuard RS4000 switches have four complementary security components, including bidirectional, stateful inspection firewall; flexible network address translation (NAT) router; secure virtual private network (VPN) gateway; and optional protection against malware using common Internet file system (CIFS) integrity monitoring (CIM).
These managed switches also act as media converters, and pass signals from the fiberoptic network to the Ethernet network and enable connection to the radio system if the fiberoptic side malfunctions. Also, the switches and FL mGuard security devices connect over a cable protected by a special lock on the connector, providing a layer of physical security. The connector requires a special key to add or remove connections.
"Because all dispatchers and other users authenticate on the server, the system maintains a high level of access security. The server also administers permissions for individual users," Hilgenkamp explains. "On the digital network, the Ethernet switch filters data traffic, allowing communication to take place solely between the server and the crane, and drops all other data packets. From there, the systems checks data transmission via universally applicable firewall rules, requiring only minimal customization for the individual cranes. The strict separation of input and output rules and their concise descriptions in table form help simplify the configuration, while the web-based GUI allows adapting the rules to meet changes in the network structure.
"For example, the firewall rules ensure that the system doesn't inadvertently communicate with the wrong crane, and that the controller continues performing its tasks without running into network overload problems. These rules also reliably eliminate the risk of access and tampering by unauthorized persons or an external service. The log file can also help determine if communication occurred with the cranes, and reconstruct the history of the IP address used to determine where and when it was used. While performing maintenance, the crane maintenance staff can activate a special firewall rule set via the so-called 'User Firewall,' allowing them to load updates or check the availability of replacement parts. Security certificates installed on FL mGuard ensure its configuration remains fully protected, and it also provides added security against spoofing and man-in-the-middle attacks."
Dan Schaffer, business development manager for networks and security at Phoenix Contact, reports, "There's a lot of fear out there about network security, but there's also a lot more awareness and collaboration between IT and engineering on addressing security, though it's a slow evolution. So, while we're mainly a components company, we started our Control Industry Solutions (CIS) group about 18 months ago to pull some of these issues together, such as deciding what controls, network and other programs work best together, or what network architecture and protection is most useful in a particular application."
SEE ALSO: Monitor and Mend Network Health
Figure1: An army of cranes and automatic guided vehicles (AGVs) uses hardwired, fiberoptic and wireless networks protected by managed Ethernet switches/firewalls, VPNs and hardware to securely coordinate container unloading and loading, and move 7 million tons of cargo per year at the Port of Rotterdam.
Source: ECT and Phoenix Contact
Defense at a Distance
While some machines and production lines retain traditional standalone postures, most are networked within their facilities and increasingly are tied to business-level networks and all their accompanying risks and needs for security.
KMT Waterjet Systems in Baxter Springs, Kansas, wanted to improve its global service by centrally diagnosing the operating status of all its Streamline ultra-high-pressure pumps, and managing and performing service-related control tasks via a secure dial-in and firewalled Internet connection.
As a result, KMT integrated at least three Ethernet links on each high-pressure pump to connect to its HMI, PLC and local firewall, which performs a dual function. It prevents unauthorized access to the pumps locally by filtering for Internet protocol (IP) or media access control (MAC) addresses, and converts IP addresses with NAT technology because each high-pressure pump worldwide must have the same IP address on the HMI and PLC for service reasons. The company's network topology for its pumps include Eagle mGuard switches with VPN capability and Spider 5TX EEC connection components from Hirschmann, a division of Belden.
To reduce the need for trained technicians to configure IP addresses locally, KMT also adopted a USB auto-configuration adapter (ACA) for redundant storage of the firewall parameters. However, to allow secure dial-up connections to the pumps, a second firewall system with a VPN option is incorporated in the customer's control center. This firewall is identical to the local firewall, and is also equipped with another ACA. This ensures a consistent service concept and high security, even for access via the Internet.
Good Advice, Better Practices
While improving an application and network's security can seem overwhelming and unapproachable at first, it's actually very similar to most control and automation projects.
"You have to own your network," says Mariam Gallegos, product specialist for networks and security at Phoenix Contact. "You have to know what you have, and then you have to find out all the access points and vulnerabilities in your network, and know where it's weak and where someone might get in."
Once inventory and awareness are achieved, Gallegos adds that Layer 3 managed Ethernet switches can be deployed to check IP and MAC addresses, define communication routing, and perform NAT tasks to provide protection in a segmented network.
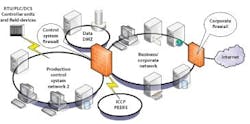
Figure 2: A digital demilitarized zone (DMZ) between a corporate local area network (LAN) and a control system LAN adds a layer of protection because no communication takes place directly from one LAN to the other, according to the U.S. Industrial Control Systems-Cyber Emergency Response Team.
Source: ICS-CERT
Similarly, the U.S. Industrial Control Systems-Cyber Emergency Response Team recommends several strategies for segmenting a company's manufacturing and business networks, and protecting them from external threats. One of these consists of a digital demilitarized zone (DMZ) between a corporate local area network (LAN) and a control system LAN adds a layer of protection because no communication takes place directly from one LAN to the other (Figure 2).
Besides segmenting and firewalls, defense-in-depth must include network traffic monitoring and malware scans of internal communications, says Mike Baldi, chief cybersecurity architect at Honeywell Process Solutions. "Many of these tools, like Network Intrusion Prevention Systems (NIPS) or Network Intrusion Detection Systems (NIDS) and deep-packet inspection firewalls, come from the IT side, so we're adapting them for process control networks. The good news is that scanning and benchmarking are easier for process control because we already have many rules about who can talk to whom, and it will be simpler for us to detect traffic deviations."
Collaboration Key to Security
Surprisingly, one of the main tools that veteran end users employ to improve their network security is simple human collaboration.
"From the beginning of a project, we put in a cross-functional team to handle network security," said Tom Moroney, manager of deepwater technology deployment and geosciences at Shell Exploration & Production at Honeywell Users Group 2013 this past June. "This team includes both our IT division and Shell's leadership. We're migrating our Well Reservoir Facility Management (WRFM) program to an interrelated, four-pillar structure, which includes understanding assets; knowing the risks and uncertainties of each; deciding how they need to be instrumented; and how to capture, store, analyze and consume data from them. This means all kinds of tools and software have to fit together and operate securely, and so we must be able to talk to our IT and our global architecture departments, and then look for suggestions from suppliers like Honeywell."
Shell has six floating and four fixed structures in the Gulf of Mexico and two floating, production, storage and offloading (FPSO) vessels in Brazil, and together they operate about 200 wells that produce 400,000 to 600,000 bpd. "They also run abut 20,000 OSIsoft PI tags or sensing and measurement points, which generate about 410 million data points per day, covering everything from complex well geometries to oil reservoir management and beyond," Moroney explained "We wouldn't be able to process all that data if we couldn't pay attention to integrating it securely."
Similarly, Dow's Cosman adds, "I would describe our cybersecurity program as a collaborative effort between our IT and operations groups, involving expertise and experience from both areas. Detailed knowledge of information security comes largely from IT, while the knowledge and experience of the specific needs and constraints associated with manufacturing facilities comes from operations. In my opinion, this type of partnership or collaboration is an essential first step in adequately addressing the security of plant level systems."
With such a working partnership in place, Cosman says the next step is to have an accurate and current inventory of the systems to be protected, followed by a strategy for organizing these systems into a documented architecture based on principles like network segmentation, defense in depth and least privilege. Detailed information about what is required here is provided in the ISA-62443 standards [see "Cooperation on Cybersecurity Standards" sidebar].
"We also maintain relationships with and participate in selected external parties, such as standards development organizations like ISA, government agencies such as the U.S. Dept. of Homeland Security, and trade associations for information sharing and benchmarking," Cosman adds. "The nature and degree of this type of external engagement has to be driven by business interests and is often constrained by resource availability."
Upcoming, Everyday Security
Security has become less dramatic and grown closer to the routine safety and maintenance tasks that operators and technicians carry out every day, and that's because many users and developers' understanding of security evolved from putting up a set-and-forget barrier to ongoing inspections of their networks, traffic and data.
"We see network routers and firewalls being combined with integrated switching functions and vice versa, and this convergence indicates security will be built into more control products in the future," Gallegos says. "In fact, antivirus, anti-malware and whitelisting capabilities are already showing up in some PLCs and I/O devices on networks. For example, we already do CIM scans of industrial computers, not necessarily to find viruses, but just to build a baseline database. This can help us look for deviations in the file system later, and then set up alerts, which can be a big help in improving security and configuration management in the future. For instance, having a test, identification and alert for altered executable files would have identified Stuxnet or other zero-day exploits before they were eventually found by antivirus programs."
Cosman adds, "I can't predict the future, but the trends I see include an increasing level of integration of security technology into industrial control systems out of the box. This trend has been in place for a few years now, and I expect it will continue. The other trend I've observed is an increasing shift from network security to a broader view of system security — embracing the people, process and technology aspects of the overall automation system, including functions from manufacturing operations down to and including safety systems and machine controls. I also believe that as the various standards and practices continue to mature, we'll be able to demonstrate that the landscape is not as confusing as it appears. Again, much if not most of the standards related material is converging on the IEC 62443 series."