“Protecting IIoT data during the lifecycle of systems is one of the critical foundations of trustworthy systems,” says Bassam Zarkout, executive vice president, IGnPower. “To be trustworthy, a system and its characteristics, namely security, safety, reliability, resiliency and privacy, must operate in conformance with business and legal requirements. Data protection is a key enabler for compliance with these requirements, especially when facing environmental disturbances, human errors, system faults and attacks.”
Zarkout is one of the authors of “Data Protection Best Practices,” a white paper published by the Industrial Internet Consortium (IIC).
"Although the white paper can be stand-alone, much of the content is aligned with existing standards and generally available documents," says Niheer Patel, product manager at Real-Time Innovations (RTI) another one of the authors. "It also fits well with other best-practice documents from the IIC, especially the Industrial Internet security framework (IISF). The paper breaks down the topic of security into the critical components and starts to address concepts, such as prerequisites to building a trusted system, interdependencies between some of the different technologies, where and when they should be applied and what the impact could be. We try to summarize, succinctly for those who don't have a lot of time on their hands."
When the team started working on the white paper, it pondered the definition of data protection. "We asked many people," says Zarkout. "People with a security background would say data protection is data security. People with a data-privacy background would say data protection is data privacy. In fact the P in GDPR, the European Union privacy law, is protection."
The data-protection umbrella
The term, “data protection,” was used as an umbrella term including security, integrity, privacy, residency and a number of other adjacent domains that utilize security mechanisms to support and empower the processes they involve, explains Zarkout. Others may define it simply as data security, but it is more.
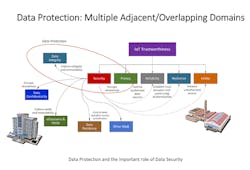
Data protection can be thought of as an umbrella covering adjacent and overlapping domains (Figure 1). "The overall diagram illustrates the different domains, positions them and describes some of the relationships between them," says Zarkout. "Notice that security plays a central and critical role in the data-protection domain. Protection is not necessarily equal to security, but security plays an enabling part in integrity, confidentiality and hold residency, and it also touches on the physical aspects of the system reliability, resilience and safety. In other words, a lack of security may lead to safety issues, for example."
Figure 1: Data protection is the super-domain covering many of the other domains such as data integrity, security and privacy and other related and connected aspects.
(Source: IGnPower)
Data at rest, in motion and in use
"A data-protection best-practice discussion must also address the best practices for data at rest, data in motion and data in use," says Zarkout. "These are the three main states that data can exist in. Data protection is important in each of these three states and others."
Some of the documents and techniques used for data protection depend on its state. Different types of protection are needed, depending on whether data is at rest, such as stored in a database, data is in motion, such as when transmitted from the cloud to an HMI, or data is in use, such as when being consumed by a controller on the factory floor.
"Another important point is that, when you say data protection for an IoT system, you really need to have a lifecycle perspective of what data protection is," says Zarkout. "The data needs to be protected throughout the lifecycle of the system and of the IoT data. The two are not necessarily the same."
A data breach may lead to multiple consequences. "It may involve data that is private in nature highlighting the need for privacy controls, restrictions and obligations," says Zarkout. "That same data can be confidential from a business point of view, highlighting the need for confidentiality, which is different from privacy concerns. Multiple domains in the organization must be looked at, and each may have different stakeholders."
Data privacy and integrity
"In addition to data security and a big part of the paper, adjacent domains are also discussed," says Zarkout. "Data privacy is one of those domains with many processes. However, it relies on data security to implement some of these processes. These domains are all part of the data-protection super-domain."
Production and manufacturing are big use cases in the IIoT. "It's important to be sure we do all the right things needed for data-centric assets," says Apurva Mohan, Industrial IoT security lead at Schlumberger and another one of the paper’s authors. "This area of data security provides all the enablers. If you look at the IIoT, it's difficult due to the many types of physical equipment. We are working with many brownfield devices; there are very few greenfield devices. If you want to provide hardware root of trust, what is the right way? The white paper tells what is to be done. How it is to be done involves other hardware and resources that are available."
In the IIoT, such as a factory floor or a manufacturing plant, there are different types of data going to and from the cloud. "On the plant floor, there is a manufacturing physical asset with sensors and actuators attached to it," say Mohan. The sensors are looking at the process variables, such as pressures, speeds and positions, and then this data is being sent back to the cloud to optimize the physical process through diagnostics, maintenance management and related apps. This is industrial data, which has minimal privacy considerations.
The other type of data is control data that moves between different types of controllers, PLCs, RTUs and HMIs, continues Mohan. "This type of data sometimes goes to the cloud for data logging and analysis and can be read from the cloud, if needed," he says. "It is equipment- and machine-sensitive data, but, again, there are not privacy concerns. Only when the user comes into the picture, do we have privacy concerns."
Data integrity and protection is applicable to all categories of data, whether it is coming from the physical asset or the human users. "Data privacy must still be considered,” says Mohan. "For example, if using an email address as a username to access an HMI, data privacy must be considered."
Privacy has been a big focus. "From the bottom-side up, all things associated with an individual can become a point-of-interest attack,” says Mohan. “If a car, which is basically a machine, is related to an individual or family, they can be tracked. Knowing their location can become a privacy issue. If the car goes to a medical clinic every Saturday, it can be inferred that the driver or passenger has a medical condition."
Data-protection team
Data protection is a team sport, not an individual sport. "Multiple stakeholders may need to be involved in making design decisions," says Zarkout. "It's not just up to the security people or the production people, depending on the use case. It cannot be the sole domain of the security people because of the adjacent implications. The safety people must often be involved."
You need to look at the whole supply chain of the solution for data protection, not only the hardware chips or at the design, continues Zarkout. "The data protection concerns will affect the hardware manufacturers, the integrators, the developers, the deployers of the solutions and the operators of the solutions," he says. "Each one of these parties may have a different set of responsibilities toward data protection."
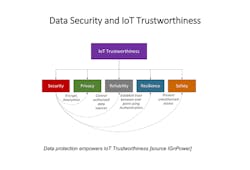
It all focuses in on IoT trustworthiness (Figure 2). "Trustworthiness is a term used a lot in the IIC community and other organizations," says Zarkout. "It refers to the fundamental notion that IT and OT are converging, or at least are starting to touch each other. And culture in IT is much different than culture in OT. OT tends to be concerned with safety, resilience and reliability, where IT is more concerned on security and privacy. Those domains cannot be looked at separately. They need to be looked at together, especially where you have interdependencies in these five elements of IoT trustworthiness. As documented in industry cyber attacks, a deficiency in security can lead to safety issues and vise versa."
Figure 2: IoT Trustworthiness converges OT's data safety, resilience and reliability elements with IT's security and privacy elements.
(Source: IGnPower)
The IIC is true to its mission. "The mission of the IIC is not necessarily to issue standards, but to explore, investigate and bring IoT technology closer to the application domain," says Zarkout. "The vendors can then collaborate within the IIC community and learn more about the different aspects, take the lessons and use them in their designs and practices within the market.”
ALSO READ: The accumulating case for deterministic control
Control Design Newsletters
About the Author

Dave Perkon
Technical Editor
Dave Perkon is contributing editor for Control Design. He has engineered and managed automation projects for Fortune 500 companies in the medical, automotive, semiconductor, defense and solar industries.