Engineering workstations and SCADA servers top the list of riskiest devices
Findings from cybersecurity firm Armis, which tracks more than three billion assets through its asset intelligence and security platform, revealed what operational technology (OT) and industrial control systems (ICS) devices pose the most risk to critical infrastructure industries in manufacturing, utilities and transportation. Engineering workstations, supervisory control and data acquisition (SCADA) servers, automation servers, historians and programmable logic controllers (PLCs) top the list (Figure 1).
Armis said that engineering workstations are the OT devices that received the most attack attempts in the industry in the past two months, followed by SCADA servers. 56% of engineering workstations have at least one unpatched critical severity common vulnerability and exposure (CVE), and 16% are susceptible to at least one weaponized CVE, published more than 18 months ago.
Uninterruptible Power Supplies (UPS) are the third device type that suffered the most attack attempts in the past two months, and 60% of UPS devices have at least one unpatched critical severity CVE.
PLCs are next in line, with 41% having at least one unpatched critical severity CVE, and Armis’ research highlighted that PLCs can be susceptible to high risk factors such as end of support hardware and end of support firmware.
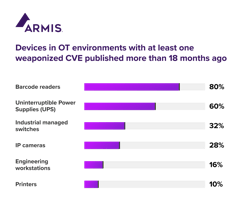
The following devices also represent some additional risk to critical infrastructure industries with one weaponized CVE before January 2022: 85% of barcode readers, 32% of industrial managed switches, 28% of internet protocol (IP) cameras and 10% of printers (Figure 2). OT environments often have multiple locations, multiple lines of production and complex distribution lines, which can make managing devices and their networks more complicated, Armis said.
“In an ICS environment, it's pretty common to have vulnerable devices, so professionals need to see what assets are on their network and additional intelligence on what those devices are actually doing,” said Nadir Izrael CTO and co-founder of Armis. “Contextual data will enable teams to define what risk each device poses to the OT environment so that they can prioritize remediation of critical and/or weaponized vulnerabilities to quickly reduce the attack surface.”
While the information technology (IT)/OT convergence is driving some cross-domain collaboration, more is needed to focus on device security, Armis said. According to the company’s research, four out of the five riskiest devices run Windows operating systems, showcasing how a basic understanding of asset risk and securing vulnerable assets is still a challenge for some IT and OT teams.
Armis looked at device types and found that many are more exposed to malicious activity because they are using the SMBv1 protocol, end of support operating systems and many open ports. SMBv1 is a legacy, unencrypted and complicated protocol with vulnerabilities that have been targeted in the WannaCry and NotPetya attacks. While security experts previously advised organizations to stop using it completely, the data shows it is still preeminent in the field, Armis said.
“From an organizational perspective, having a risk-based approach to vulnerability management must go hand in hand with OT and IT departments working together to help coordinate mitigation efforts,” Izrael said. “Cross-departmental projects will help streamline process and resource management and achieve greater compliance and data security. Overall, to navigate the challenges of the new industrial era, security professionals need an IT/OT convergence security solution that shields all assets connected to the network.”