Decoding Industry 6.0: Navigating the convergence of automation, safety and cyber resilience
Key highlights
- The critical and evolving role of networked safety systems such as CIP Safety, ProfiSafe and FSOE in modern machine design highlight the importance of deterministic communication and accountability for safety actions.
- Understanding and applying risk assessment, including HRN and PLr, is as a legal requirement and a fundamental step in the machine building process, directly impacting the selection and implementation of safety components such as MTTFd, DC and CCF.
- The shift toward Industry 6.0 necessitates a broader skillset for controls engineers, requiring knowledge of IT/OT convergence, moving beyond the Purdue model with technologies like MQTT and OPC UA, diverse network topologies and embedded cybersecurity within the OSI model.

Emerging Technologies & Architectures of Automated Systems with Integrated Functional Safety
LINDA CARON
PARKER HANNIFIN
Industrial revolutions have taken place almost every century since the 1700s. Now, they occur every decade.
Industry 4.0 was the start of networking systems together, also known as the Internet of things (IoT), from 2010 to 2020. Today, Industry 5.0 has modernized Industry 4.0 with the addition of cyber-physical systems, cognitive systems and artificial intelligence (AI), from 2020 to 2030. If I had a crystal ball, I would see Industry 6.0 as the human element of functional safety. We need to bring together autonomous machinery, digitization, AI and, of course, cyber resilience.
What’s driving all of this? The need to rebuild the North American manufacturing base, onshoring, the need to remain competitive with offshore markets, a growing population and the need for efficiency. Rising geopolitical tensions have created an increase in bad actors driving the need for enhanced cyber resilience.
The cornerstone of our continued manufacturing growth will be new legislation EU 2023/1230 mandating cyber resilience as one of the many enhancements.
The human element of our industrial growth will be hindered by a skills gap. The knowledge to operate advanced manufacturing equipment requires a broad skills base from mechanical knowledge, functional knowledge of fluid power mechanical components, an understanding of electricity and some working knowledge of electronics, advanced programming capabilities and some basic understanding of systems architecture.
Systems architecture presents in many forms. There is the Purdue model of industrial communication systems known as the automation pyramid. It is the current hierarchy of establishing the layout of IT vs. OT in a manufacturing environment. This very model is being challenged today by MQTT and OPC UA as examples of cloud-based communications models that interconnect data to a broker. The Purdue framework was designed to enhance security, efficiency and scalability by defining a structure for machinery processes to interact with each other.
There are varied network topologies, which is fundamentally how you connect the devices on your network. Examples include Ethernet, which typically is a ring topology, where IO-Link devices use a star topology. These topologies lay out the location of the IP addresses and how data will be transmitted across the network. Then, there is the OSI data model, which is the framework for network security and goes a layer deeper into the device to establish a structure for the data communication to transmit across the network.
Add cybersecurity to this, and you are adding security and encryption to devices by embedding the resilience into the OSI model’s firmware stack. So, we have hardwired systems, collective wiring; varied types of networks and corresponding protocols for communication, such as EtherNet/IP, EtherCAT and Profinet; and you can mix these and include the cloud-based wireless communication models for data gathering.
Safety added to the machine can be hardwired or networked on safety networks, which logically organize the timing and sequencing of messages. These are your CIP Safety, ProfiSafe and fail safe over EtherCAT (FSOE) protocols. These are established safety network communication protocols to ensure messages are delivered in time—deterministic—and in the proper sequence, first in first out.
The order of safety messages is critical to ensure proper function of the safety circuit. The value of safety over the network is accountability. Accountability comes in the form of knowing if the machine is down or off-line and how it was shut off—did a fault occur, or was the stop controlled by way of a safety device? Only then can you implement corrective actions to ensure faults are reduced or controlled stops are avoided by fixing the root cause of the problem.
This is a quick increase in efficiency, increase in uptime and less scrap yield. Regardless of the structure, layout and topologies used in your network, one thing is certain: a risk assessment is a legal requirement to ensure the safe function of any machine.
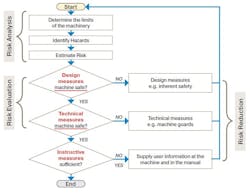
The risk assessment has three steps: risk analysis, risk evaluation and risk reduction (Figure 1). Risk analysis should be done by a qualified team of people that understands the machine function but did not design the machine—a fresh set of eyes.
Once hazards are identified, one of several risk-assessment tools can be used to estimate the risk, such as the hazard rating number (HRN) system. This will form the basis of your required performance level (PLr). Your goal is to meet or exceed your PLr in the final design or performance level.
Once the hazard is identified and the risk is estimated, it’s time to determine the best path forward. Risk evaluation looks to design out risk first. If not, risk mitigation measures are used. This can be anything from simple guarding or interlocks to any technical measure that will protect the worker.
Get your subscription to Control Design’s daily newsletter.
Note that it is important to conduct the risk assessment assuming no risk mitigation in order to avoid missing hazards. This is tricky on older pieces of equipment that may have machine guards or safety measures in place. You want to show the bare-bones hazards and what measures were used to add safety.
All of this must be documented in the risk assessment to show the risk mitigation strategies you used. Pictures and videos are often used as supplements to show safe stopping distances and measurements taken during the assessment. It is recommended to document component part numbers, serial numbers and mission time, as well; you’ll thank me when the labels wear off and you need a replacement.
When risk reduction requires the use of products such as light curtains or other safety devices—technical measures—to fulfill the safety function, it is important to calculate and document the mean time to dangerous failure (MTTFd) of the components used to ensure they meet the performance level requirements for a given degree of risk—from PLa to PLe.
Diagnostic coverage (DC) and common cause failure (CCF) must also be considered in the design of the safety circuit, especially for higher risk levels to ensure proper function and fault detection. Ultimately, we want to meet or exceed the PLr we established earlier. Failure to meet the required PLr leaves hazards on the machine.
While this is all no easy task, Industry 6.0 should be the human element of all interconnected things. We need to bridge the technology gaps and bring harmony to so many operating principles, architectures, topologies and standards.
Safety standards are working to harmonize, and, with the advancement of technology, many standards are being reviewed every four years, instead of five. If you are retiring, I congratulate you. If you are young, I encourage you. Great opportunities in advanced manufacturing are limitless with hard work and dedication.
About the Author
Linda Caron
Parker Hannifin
Linda Caron, global product sales manager, functional safety, Parker Hannifin, pneumatic division, will join Eric Lanke, president/CEO, National Fluid Power Association, to present "Emerging Technologies & Architectures of Automated Systems with Integrated Functional Safety" at 1:30 pm on May 14 during A3's Automate 2025 in Detroit. Caron specializes in functional safety for industrial machinery and has achieved the Functional Safety Engineer (FSE) and Certified Machinery Safety Expert (CMSE) certifications from TÜV Nord. She holds degrees in chemical engineering, business marketing and fluid power. With more than 30 years of experience in fluid power and the electrical industry, Caron has specialized in functional safety for the past 17 years and has supported many industries from food and beverage to oil and gas in this capacity. She can be contacted at [email protected].