How machine builders can prepare for the IIoT
Industrial control systems have expanded from simple analog 4-20 mA communication schemes that allow one-to-one connections to advanced digital protocols such as Fieldbus. These technological advancements have resulted in faster communication times and reduction of non-recurring engineering costs, according to “Introduction to Fieldbus,” a 2006 white paper written by Moore Industries.
Today, the Internet of Things (IoT) presents an abundance of new opportunities to make these systems even faster and more reliable. As Industrial IoT (IIoT) devices become more accessible and innovative, it is important to further understand how the technology impacts and benefits current industrial systems.
The IoT is a phenomenon in which reduced hardware and software costs enable the embedding of Internet-connected computers on everyday objects—“things.” These computers provide insights into the physical world such as room occupancy, water flow through a pipe, or power outages in a city, similar in many ways to industrial control systems.
What makes the IoT truly outstanding, however, is that this data can be communicated to any data processing center in the world. The power of cloud computing is thus made available to local control systems, which means more complex data aggregation, pattern detection and diagnoses can be performed.
Technology benefits
One example of the power of the IoT is found in Siemens’ Electronic Works factory in Amberg, Germany. The factory uses Siemens’ own Digital Enterprise Software Suite (DESS) to produce programmable logic controllers (PLCs) at an impressive rate of one per second with 99% reliability and 100% defect traceability, according to “The Dawn of the Smart Factory,” a 2013 article in IndustryWeek. Despite the impressive statistics, however, that has not always been the case—and definitely not before the emergence of the IoT.
When first established in 1989, the factory recorded a defect rate of 500 defects per million; today it records a minuscule 12 defects per million while producing seven times as many products, according to “Defects: A Vanishing Species?” on Siemens website. This is despite having a relatively unchanged amount of workspace or number of employees. The real change lies in how software is used. Modern software frameworks such as the DESS combine smart-device communication, Internet connection to external production systems and traditional automation techniques to deliver such monumental results.
This increase in industrial productivity is because IoT is often referred to as Industry 4.0 or the Industrial Internet, according to “Design Principles for Industrie 4.0 Scenarios: A Literature Review,” a 2015 working paper written by Mario Hermann, Tobias Pentek and Boris Otto of Technische Universitat Dortmund in Germany. It is expected to bear similar historical weight as the invention of mechanical machinery or the use of electronics to control industrial processes.
The upgrade to these cutting-edge operational standards, however, will not only be measured in currency, but also in overcoming roadblocks since machine builders will now have to go beyond guaranteeing performance and reliability in their products; they will also need to provide assurance of privacy, authenticity and integrity.
Technology impact on privacy
In isolated control systems, privacy is measured in terms of the access granted to the control servers, according to “Data security guidance,” a 2015 paper on Ireland’s Data Protection Commissioner website. Generally, a high user level such as operator or engineer is required to gain access to the process data and control mechanisms.
Since the focus of machine builders is currently on the quality and reliability of their products, the level of protection provided by server applications is often overlooked. Nevertheless, this will gradually change as the intelligence of industrial systems—and thus their security—becomes more decentralized. Field devices and composite machines will begin to have increasingly more authority on the data that they produce. As such, machine builders must now have their products protect this data to ensure its privacy.
Technology impact on authenticity
To achieve data protection at the device level, there must be some way of authenticating the user who is requesting the data. There are two ways of doing this. First, each device should know at the time of installation or update which users can be trusted. The device should then only provide the data to those specific users in an encrypted fashion. The initial trust by reference provides the device with partial trust for users in the system. Encryption adds an additional layer of protection as the data moves about the network.
Also read: Cybersecurity: Who can hack it?
Second, there must be a commissioning process to integrate the device into its industrial ecosystem and to establish its trustworthiness—that is, to ensure that it is not an illegitimate device which may contain malicious software. This provides the control network with trust on the field device. These trust requirements provide the foundation for secure authentication for smart industrial systems.
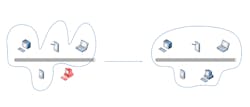
Computer networks are generally focused on connecting network nodes, including computers, devices and machines in an efficient manner. As a result, reliability and security are not inherently built into the networks and are instead delegated to the nodes themselves. This lack of information assurance or security leaves nodes with no guarantee that the other nodes with which they interact are not malicious. It also doesn’t guarantee the system as a whole that a malicious node won’t join its ecosystem (Figure 1). To solve this problem, an authentication mechanism must be used.
Figure 1: The network on the left consists of devices that trust each other. Adding a node to the network as in the right raises two issues: the network does not know whether it can trust the new node, and the new node does not know which other nodes to trust in the network.
Starting with an empty subset of trusted nodes, nodes outside of the subset can be added to it as they become authenticated. The process of adding nodes to this subset of known and trusted nodes is known as commissioning (Figure 2). This is not a new concept since device commissioning is already available in protocols such as HART for analog systems or Fieldbus for digital systems. However, the focus of these commissioning protocols is integration into the system and validation of the device’s functionality—not security and trustworthiness. This needs to change with the proliferation of the IoT.
Figure 2: A device being commissioned entails being moved from a status of unknown and untrusted to known and trusted.
Secure commissioning can be accomplished in two ways. One of them is to rely on a third party for the authentication of each device. By having a database naming the devices that can be trusted, the control system need simply query the database when a new device is added to it. If the device is found, then the device can be integrated into the rest of the system and have its functionality tested. This is similar to the way commissioning currently works in the Fieldbus protocol with the exception that the database for an IoT ecosystem will be remote rather than local. Problems with this approach include that in order to ensure that a device is approved by the manufacturer, a global database, which may not be always available, must be accessed. Further difficulties would arise because of the heterogeneity of manufacturers and their individual means of approving new devices for use.
An alternative exists in commissioning based on reputation systems, according to “Improving Security for SCADA Sensor Networks with Reputation Systems and Self-Organizing Maps,” written in 2009 by José M. Moya and numerous other academics at Spain’s Universidad Politécnica de Madrid. In these systems, a device is given a “reputation” value by other devices and propagated to the entire network. This reputation value gets lowered whenever the device displays anomalous behavior such as not forwarding information, delaying it or performing actions when not commanded to do so.
The result of this loss of trust is that the device gets ostracized, and information is not shared with it any longer—in other words, it is selectively decommissioned. Therefore, this commissioning mechanism works by granting a device an initial level of trust and removing it when it displays bad behavior whereas a centralized commissioning mechanism starts off with no trust and grants full trust once authentication has taken place.
Technology impact on integrity
The third and final feature composing a secure industrial system is integrity. Integrity means that only the right users can modify the right data. For example, set points in a system should only be modifiable by authorized operators, and logs should be modifiable only after a pre-specified procedure is followed by an authorized user. The methods of authentication also serve to preserve integrity. However, other practices can aid it even further.
Data backups are essential to maintaining a snapshot of a system at any point in time, and, since costs in memory have been in constant decline for over half a century, according to John McCallum’s IT website, this is a task that is immensely more feasible today than ever before. According to “Expect Sensor Prices to Fall,” by James Carbone on Digi-Key Electronics’ website, similar drops in the price of sensors also make it possible for machine builders to increase the redundancy of data by adding more measurement points per variable—for example, using 10 temperature sensors for a single reading, instead of just one.
Conclusions
By creating products that collaborate to ensure privacy, authenticity and data integrity, machine builders can securely harness the power of smart devices, the cloud and the Internet of Things. First, the data generated by field devices must be protected from access or modification by unauthorized users. Second, there must be a mechanism of authenticating a new field device to the system and network users to the new field device.
Finally, the data generated by machinery should be acquired from redundant sources and backed up regularly to help ensure integrity. Overcoming these security challenges will require extensive learning, training and testing, but it will be worth the increase in productivity and reliability that the IIoT will bring.
Anthony Skjellum, PhD, is the lead cyber scientist for AuburnUniversity and
director of the AuburnCyberResearchCenter. He has been a professor of computer science and software engineering at Auburn since 2014. Contact him at [email protected].
Janice Cañedo is a PhD student at AuburnUniversity working on Internet of Things research. She holds a bachelor’s degree in computer science from ColumbusStateUniversity. Her work includes innovative security design of malware, network structure, operating system resiliency and data analytics for IoT systems. Contact her at [email protected].
Carlos Lemus is a graduate student at AuburnUniversity. He helped to lead the formation of Auburn’s Internet of Things Laboratory and has experience working on systems ranging from industrial controls to onboard networks for commercial airplanes. Contact him at [email protected].

Leaders relevant to this article: